
Cryptocurrency Exchange Poloniex had its wallets drained in the second biggest Cryptocurrency hack of 2023. Over 4900 ETH were siphoned from Poloniex’s Hot Wallet 4 by the attacker and distributed across multiple accomplice wallets.
The attackers seem to have timed this attack around the recent pump in the market, possibly to try and siphon as much liquidity as possible.
NOTE: If you’re a Poloniex user, the company has confirmed that user funds are 100% safe and have not been affected by the hack but you should probably consider moving your coins to another exchange or preferably a hardware wallet, at least temporarily.
Now let’s dive into this exploit, covering how it was discovered, what vulnerability was exploited, and what the aftermath of the attack is.
How was the Poloniex Hack Detected?
Around 10:55 UTC security firms, PeckShield and Cyvers flagged a potential exploit on Poloniex’s hot wallets. PeckShield published a relatively unassuming tweet, linking to one of the compromised wallets.
Cyvers made a similar post but eventually followed up with more context saying their AI detection system estimates around $54 million were moved to a suspicious address.
The hack was indeed confirmed by Poloniex 12 minutes later. What made this attack special was that the hackers continued to siphon funds in multiple transactions until Poloniex’s wallets were drained.
Although Poloniex acknowledged the attack relatively quickly, the first new minutes during an ongoing exploit are the most important ones when it comes to damage limitation.
According to Lossless DeFi, a company specializing in on-chain exploit detection tools, Poloniex could have saved over $45 million USD by employing an exploit detection tool.
Without one, the hackers continued their operation undisturbed until all funds were eventually stolen. It is currently estimated that over $114 million USD were stolen.
Security Firm PeckShield are actively oversee-ing all activity pertaining to the hacker’s wallets and have created a diagram that shows how the money is currently moving:
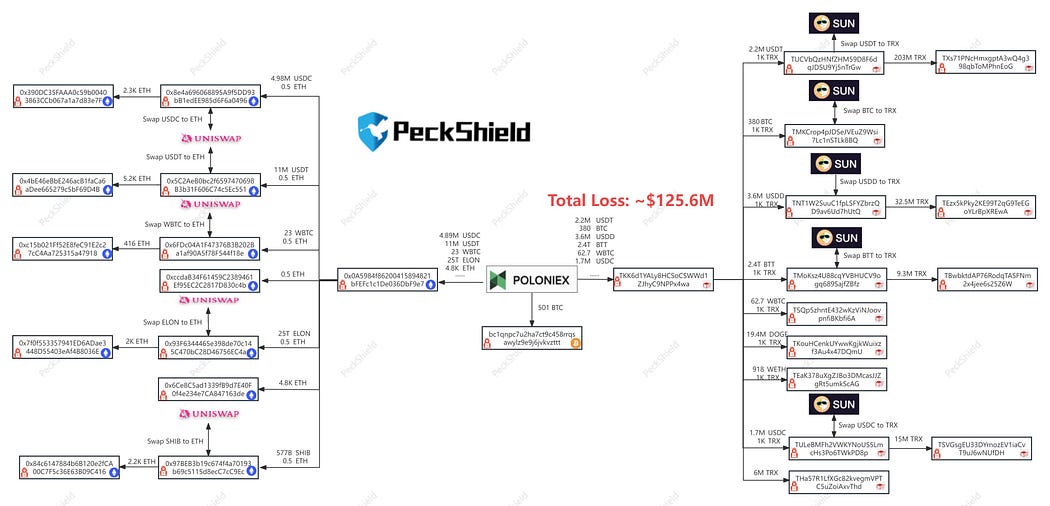
It is fascinating that we get to see this live as it is unfolding. The transparency that blockchain provides allows us to learn from our mistakes and hopefully not repeat them again.
Who is Behind the Poloniex Hack?
The identity of the attackers is currently unknown but Etherscan along with some of Cyvers, PeckShield and Lossless DeFi were able to tag the attacker’s wallets and they remain marked on chain as “Poloniex Hacker”.
There are currently 8 known hacker addresses associated with this attack, with Poloniex Hacker 1 as the main wallet initiating the hack with a starting transaction of 4900 ETH, continuing to Siphon until Poloniex Hot Wallet 4 was empty. Here are all known hacker wallet addresses:
- Poloniex Hacker 1
- Poloniex Hacker 2
- Poloniex Hacker 3
- Poloniex Hacker 4
- Poloniex Hacker 5
- Poloniex Hacker 6
- Poloniex Hacker 7
- Poloniex Hacker 8
Poloniex Hacker 1 then continued to distribute ETH across the other 7 wallets, and is currently swapping ETH to various other altcoins and memecoins through various protocols in order to make it harder to track the funds.
How was the Poloniex Hack Possible?
According to Coindesk and CertiK — a reputable blockchain security firm, the incident was likely a “private key compromise.”
Now, how the Hot Wallet’s private key came to be compromised, is an entirely different story. Security researcher Officer’s Notes limits the vector of attack to either social engineering or malware injection.
Once more information comes to light — I will make sure to update this section of the article!
Next steps for Poloniex
Poloniex has put up a 5% white hat bounty if the hacker chooses to return the stolen funds. If the attackers take the deal, they can walk away without being prosecuted, and with just over $5 million in the bank.
You’d have to be a special type of idiot to say no to that kind of deal, and instead choose to live the rest of your life on the run, hoping that you’ll continue to evade the law and get to enjoy the money that you have stolen.
With this kind of attacks, there is always the possibility that North Korean hackers could be behind them, in which case the white hat bounty will most likely be rejected.
Poloniex have given the attackers 7 days to return the funds, before they involve the law.
This marks the second biggest crypto hack this year. Due to blockchain technology and the fact that everything is recorded in a public ledger, we have unprecedented access to how these attacks operate, and more importantly, we have the opportunity to learn from them, and create better systems that are more secure, and faster to act then a crisis situation does show itself.
That’s all I have for today, show this article some love (👏) and follow me for more.
Finally, if you’re into Algorithmic trading — check out algorithmic cryptocurrency trading platform Aesir! Aesir is a state-of-the-art trading platform that allows you to build complex crypto trading bots and maximise your gains.
Thank you for reading!
Enjoyed this article?
Sign up to the newsletter
You’ll receive more guides, articles and tools via e-mail. All free of course. But if you value this blog and its educational resources, you can subscribe to become a paid member for only $3 a month. This will keep the website open and free.
